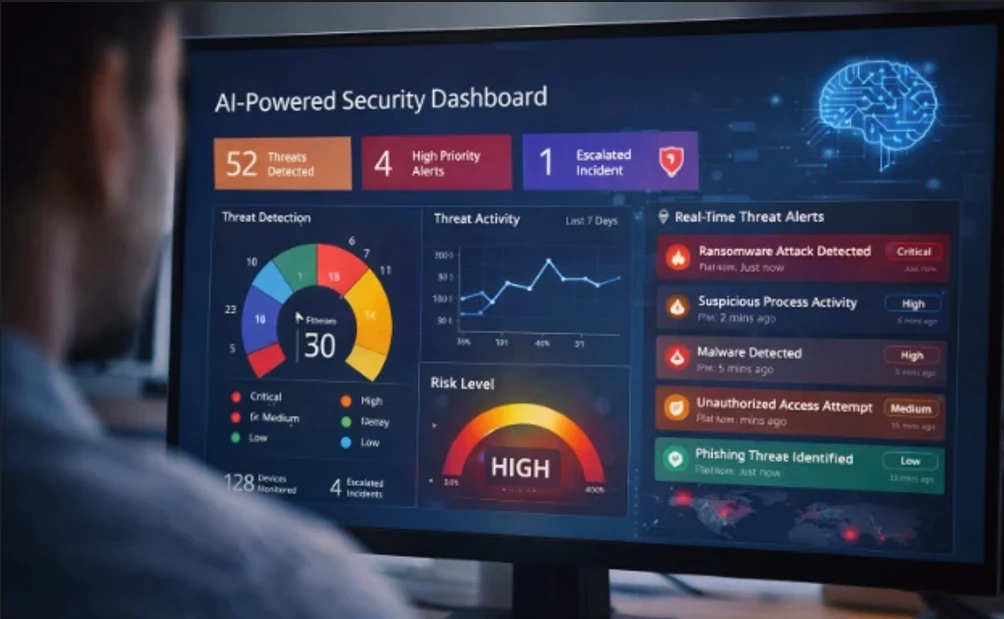
If you’ve ever been caught off guard by a cyberattack or had your personal data compromised, you know just how important it is to safeguard your devices. I’ve been there, and nothing gets your heart racing quite like seeing a pop-up telling you your system has been breached.
Since then, I’ve learned just how crucial endpoint security is for keeping data secure. It’s not enough to rely on basic antivirus software anymore, especially with the evolving nature of cyber threats.
That’s where leading endpoint security solutions come in. The best tools use AI and behavioral analysis to proactively detect and neutralize threats, ensuring that your devices remain secure no matter what. Let’s explore why AI-driven endpoint security solutions are now more essential than ever, and which key features make them stand out.
What Are Endpoint Security Solutions and Why Do You Need Them?
Endpoint security solutions are designed to protect the devices that connect to your network, such as laptops, smartphones, and workstations. These solutions do more than just prevent virus infections—they protect against advanced cyber threats like ransomware, malware, and unauthorized access.
The rise in remote work has made endpoint security even more critical, as employees now connect to the corporate network from various locations and devices. The right solution ensures that these endpoints remain secure, no matter where they are.
It’s no longer just about keeping threats out—it’s about actively monitoring and responding to emerging risks in real-time.
What Features Should You Look for in Endpoint Security Solutions?

When choosing an endpoint security solution, you want something more than just basic protection. The right tool will be tailored to detect advanced threats, simplify management, and provide detailed insights into your network’s health. Here are the top features I suggest looking for:
1. Next-Generation Antivirus (NGAV)
Traditional antivirus software focuses on identifying known threats, but next-generation antivirus (NGAV) uses machine learning and behavioral analysis to detect previously unseen or zero-day threats. With NGAV, you get a deeper level of protection that goes beyond signature-based detection.
2. Endpoint Detection and Response (EDR)
EDR tools monitor your devices continuously and provide real-time data collection. They allow for immediate threat detection, investigation, and automated responses. If a sophisticated attack is underway, EDR helps identify it early and block the threat before it spreads.
3. Centralized Management Console
A centralized management console makes life a lot easier when you’re managing multiple devices. From a single dashboard, you can deploy updates, manage policies, and respond to incidents across all your devices, saving you time and reducing the chances of human error.
4. Ransomware Protection & Recovery
One of the biggest threats today is ransomware. Look for solutions with built-in protection against ransomware, such as behavioral monitoring and automatic file rollback, to ensure that even if an attack occurs, your files are recovered without paying the ransom.
5. Cross-Platform Compatibility
Given the variety of devices employees use today, including Windows, macOS, Linux, and mobile platforms, you’ll need an endpoint security solution that provides consistent protection across all operating systems. This ensures that all your devices are safe, regardless of their platform.
How to Choose the Right Endpoint Security Solution
When deciding which endpoint security solution is best for your team or organization, here’s a step-by-step guide to ensure you’re making the right choice:
Step 1: Assess Your Needs
Take some time to assess what your devices need. Do you have remote workers? Are you managing a large number of devices, or just a few? Are you more concerned about data loss or unauthorized access? Knowing your priorities will help you narrow down the features you require.
Step 2: Look for AI-Powered Protection
AI-driven protection is becoming a must. AI can analyze patterns, detect anomalies, and respond to threats in ways that traditional methods simply can’t. It’s important to choose a solution that integrates AI and machine learning to enhance detection and reduce false positives.
Step 3: Consider the User Experience
Security shouldn’t come at the cost of usability. You want software that’s easy to install, configure, and manage without requiring too much time or effort from your team. Simplicity in operation is key, especially when managing multiple endpoints.
Step 4: Evaluate Reporting and Support
Effective reporting and customer support are essential. A good endpoint security solution should offer detailed logs and easy-to-read reports on system health, detected threats, and response times. Additionally, 24/7 customer support can be invaluable during critical times.
Frequently Asked Questions
1. What’s the difference between traditional antivirus and NGAV?
Traditional antivirus software relies on known signatures to detect threats, while NGAV uses AI and behavioral analysis to detect new or unknown threats based on behavioral pattern, offering much deeper protection.
2. Can endpoint security protect against all types of cyberattacks?
While no solution offers 100% protection, the best endpoint security tools provide multi-layered defense against a wide range of threats, including viruses, malware, ransomware, phishing attacks, and more.
3. How does endpoint detection and response (EDR) work?
EDR continuously monitors your endpoints for suspicious activity. If an anomaly is detected, the software can respond automatically, blocking the threat and alerting you in real-time. It provides detailed insights into the attack, allowing for fast remediation.
4. Can endpoint security solutions work across different devices and operating systems?
Yes! The best endpoint security solutions are cross-platform compatible, providing protection for devices running Windows, macOS, Linux, and mobile operating systems. This ensures that all endpoints are secured, no matter the platform.
Stay Secure with the Right Endpoint Protection
Choosing the right endpoint security solution is one of the best investments you can make in today’s cyber environment. With the constant evolution of cyber threats, having robust, AI-powered protection ensures that you can keep your devices and data safe—whether you’re at the office, at home, or on the go.
Incorporate the features we’ve discussed into your decision-making process, and you’ll find the perfect tool to safeguard your endpoints. Don’t wait until it’s too late—take proactive steps today to ensure your security stays ahead of the curve!